 |
|
|
 |
2004
May
31
|
Spam hunters / Cheese-rolling?
CNET has an interesting article today about
the
detectives who hunt down spammers.
The bottom line? Spammers always falsify their identity, but if they're really selling
anything, there's a money trail to be followed.
A spammer can't hide completely and still be able to receive anything from his customers.
But if person A wants to harm person B, and B is a legitimate businessperson,
all A has to do is send spam advertising B's product.
The money trail will lead to B, and A will get off scot free.
Spammers, when caught, routinely say this has been done to them.
Here
is an amusing report about the cheese-rollers of Gloucestershire.
|
 |
2004
May
30
|
Too busy
I'm too busy to write anything, but the BBC has a nice article about
how hippos
produce their own sunscreen.
|
 |
2004
May
29
|
C# as a first programming language
Most books about
C#
are designed for people who are moving to C# from C++ or Java.
What do you do if you want to learn C# and have not already mastered a related language?
After a day of rooting around computer stores and bookstores in Gwinnett County,
here are my recommendations:
- Start with
Microsoft Visual C# .NET Step by Step,
published by Microsoft.
This is packaged with the development software, Visual Studio C# Standard Edition, as the
Microsoft Visual C# Deluxe Learning Edition.
(When buying this used, make sure the software is still with it.)
If you are a full-time student or faculty member, you may come out better buying
the book by itself, and then spending an extra $100 on the
full Visual Studio system (C#, Visual Basic, J#, etc.)
at academic prices.
The academic version is fully functional, and my understanding is that as long as you
qualify as academic, you can use it for any purpose (including commercial work).
- After working through about 2/3 of that book (skipping the chapters that seem to
be abstruse or irrelevant), switch to
Visual C# for Dummies.
This does not imply that you are a "dummy."
The "Dummies" books stand out because they are all well-organized to meet the student's needs.
Many other "teach yourself programming" books seem to be hastily written transcripts
of whatever was on the author's mind, or rough paraphrases of language reference manuals.
A disadvantage of these books is that they don't have homework exercises, so you'll have
to self-assign projects.
A more conventional textbook that is excellent and very comprehensive
(and has homework assignments) is
Deitel's
C#: How to Program.
This is designed for Computer Science 101 and is well worth reading, though it's dense going
(hundreds of pages crammed with useful information).
If you're a business major who won't do anything unless it's obviously relevant
to "business," you may prefer Deitel's
application-driven tutorial.
As a scientist, I find it boring.
Some precautions:
- Don't get a C or C++ book by mistake.
- Don't get a book that is exclusively about ASP.NET (web pages that do computations - one of
many things you can do with C#).
- There have been two editions of Visual Studio and the .NET Framework, dated 2002 and 2003.
Get materials for the 2003 edition if possible, but it's no great loss if you use the older ones,
so long as you know you're doing it. A few features were added in 2003, and many will be
added in 2005.
- Vita brevis, ars longa. Two books won't make you an expert computer programmer.
Much of the art of programming has to do with how to arrange simple elements to perform
complex computations - not merely learning the language in which those simple elements are expressed.
Cathy and Sharon note that the preceding 3 entries in this notebook mention,
respectively, a pet rat, a pet bird, and pet peeves.
|
 |
2004
May
28
|
Device programmers under multi-user Windows XP /
Farewell, Charles
The people who program microcontrollers seem to be particularly unaware
that Windows is a multi-user operating system.
(See my recent exhortations
about bad Windows programming practices.)
Today I had adventures getting two different programmers working at our lab.
 Some literature seems to indicate that the
Advantech Labtool-48
(as opposed to Labtool-48XP)
does not work under Windows XP.
Some literature seems to indicate that the
Advantech Labtool-48
(as opposed to Labtool-48XP)
does not work under Windows XP.
That is not true.
It works just fine under Windows XP.
However, in a multi-user NTFS environment, you have to grant permission for all users
to read, write, and modify the folder C:\Program Files\AEC\WLT48.
This does not seem to be a new issue in Windows XP; it was equally a problem with Windows 2000.
 Microchip's excellent MPLAB IDE for PIC microcontrollers
seems to be massively ignorant of NTFS file permissions.
The most common error message is
Access denied.
But I even got messages from Windows that the access-control lists for certain folders were malformed,
not just incorrect.
Microchip's excellent MPLAB IDE for PIC microcontrollers
seems to be massively ignorant of NTFS file permissions.
The most common error message is
Access denied.
But I even got messages from Windows that the access-control lists for certain folders were malformed,
not just incorrect.
A quick fix is to go to a command prompt and type:
cacls "C:\Program Files\MPLAB IDE" /t /e /g Users:F
which makes the software work, but gives all users full control over the folder in which it is stored
(which may be undesirable).
Last night,
just two days after celebrating his 3rd birthday (a very ripe old age for a rat),
Charles
passed away quietly in his sleep.
For the first time in seven years, we now have no furry pets.

Photo Copyright 2003, 2004 Cathy Covington
|
 |
2004
May
27
|
Hello, Mr. Cheeps
 Yesterday afternoon, on her way to class, Cathy noticed a
baby mockingbird jumping around in the street, begging the cars to feed it.
Yesterday afternoon, on her way to class, Cathy noticed a
baby mockingbird jumping around in the street, begging the cars to feed it.
Being the animal expert that she is, she picked up this unfortunate bird,
took it into the computer graphics lab
(where it immediately became the class mascot), and
immediately used the Internet to find out how to take care of it.
It was very happy to eat a couple of beans out of her hand right away.
In due course, she brought it home, mixed up a nourishing paste to feed it,
and continued to take care of it until this afternoon, when she turned it over
to a wildlife rehabilitator
that she had contacted through a local vet.
I named the bird "Mr. Cheeps" partly because of its characteristic cry,
and partly for the sake of the pun in today's title.
When a baby bird falls out of the nest, the parents can't bring it back,
but they will continue to feed it if they can do so.
Today Cathy discovered that one of the parents had gotten run over
while trying to feed the baby in the street.
Presumably, the other parent is still taking care of the other babies,
or else the rest of the family was killed;
Cathy heard no distressed peeping in the area.
Hand-feeding a bird is an amusing enterprise.
The baby bird's routine is to peep for food about every 15 to 30 minutes all day long,
then sleep through the night and resume in the morning.
This bird quickly started to recognize Cathy as its foster mother;
it responded to her voice (peep! peep!) and enjoyed being sung to.
Being a helpless baby, it trusted her completely and enjoyed being handled.
|
 |
2004
May
26
|
Three pet peeves
\begin{grumpy_old_man_mode}
As of today I can no longer refer you to articles in the
Athens Banner-Herald
because that newspaper won't let you view its articles on line
unless you register and give personal information,
including your birth date (handy for identity thieves) and
consent to receive spam.
Since the newspaper's requirements are contrary to generally accepted safe computing practices,
all I can do is tell you that their computer will let you register with "No Name Given" in place
of each line of the name and address, and an invalid e-mail address.
I'm struggling with the ethics of this.
I think if I gave them a realistic-looking false address, it would be unethical.
As it is, they can look at their database and know what they're getting;
then they can kill my account if they like.
They've already eliminated most casual web-surfers from their audience.
For more ranting on this subject see
May 8.
The newspaper has not answered my e-mail about this matter.
Melody tells me fans of American Idol have gotten it into their heads
that Diana's home town, Snellville, Georgia, is "rural."
Snellville is to Atlanta as Burbank is to Los Angeles. Got that? Good.
And Atlanta is what Los Angeles would be if it weren't so quiet.
Warranty and warrantee aren't the same word,
and they're not pronounced alike
(except by one noted Atlanta radio personality).
A warranty is a promise, and a warrantee is a person who benefits from the promise.
They're pronounced "WARREN-tee" and "Warren Tee" respectively
(that is, warrantee sounds almost like two words).
The same distinction used to apply to guaranty and guarantee,
but now only guarantee survives, and it has both meanings.
\end{grumpy_old_man_mode}
|
 |
2004
May
25
|
Old astronomy books / Windows tip / Rat
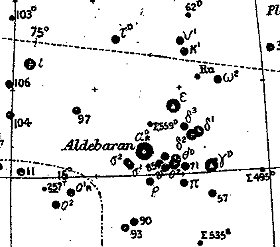 I collect Victorian astronomy books, and today's acquisition is a very well-preserved
copy of A New Star Atlas, by Richard A. Proctor
(London: Longmans, 11th ed., 1884),
which has spent most of its life in New Zealand.
I collect Victorian astronomy books, and today's acquisition is a very well-preserved
copy of A New Star Atlas, by Richard A. Proctor
(London: Longmans, 11th ed., 1884),
which has spent most of its life in New Zealand.
Here's a small part of one of the charts.
Click on it to see more of it.
Proctor was the Patrick Moore of the 1880s: he wrote a large number of popular astronomy books.
This atlas was the predecessor of Norton's Star Atlas, which came out early in the
20th Century and is still being revised and reprinted.
If you try to boot your PC and get the message:
Windows cannot start because the following file is missing or corrupt:
<Windows root>\SYSTEM32\HAL.DLL
or words to that effect, the problem very likely isn't with HAL.DLL at all.
This error message comes up if your BOOT.INI file has been deleted.
To restore it, follow the instructions here.
We have encountered a virus that deletes BOOT.INI.
Since BOOT.INI is a small text file that merely tells the computer where to find Windows on the hard disk,
it's easy to reconstruct.
Happy birthday, rats!
Tomorrow (May 26),
Cathy's last surviving
pet rat,
Charles the Great (or "Karl the Gross" as I sometimes call him),
will reach the ripe old age of 3 years.
|
 |
2004
May
24
|
Physics puzzle again / Taxing problem again
On April 20 I claimed that
if you have a sloping conveyor consisting of rollers, all initially at rest,
and you set a box sliding down it, the box will move at a constant speed
rather than accelerating as it proceeds.
This is because every time it advances a short distance, it meets another
roller that it has to set in motion.
David Stafford writes:
Can't we assume the inertia of the rollers
is the equivalent of a constant drag force? If so, it should behave
just as air does on a falling object. The object should continue to
accelerate until it reaches its terminal velocity. In this case it
should accelerate until the combination of resistance from the rollers
and air drag is sufficient to offset its weight. A relatively
lightweight object may reach its terminal velocity quickly on this
conveyor and would give the false impression that it doesn't
accelerate. But, once again, even that impression must be incorrect
because, in your experiment, the object is placed at the top and given
no outside propulsion to begin its descent (so it had to accelerate
from zero).
I'm no physicist either, but I think he's right, and I think that's what
Uncle Warren had in mind, though I reproduced his explanation imperfectly.
The rollers are just like air or water molecules that are initially at rest
and have to be set in motion by an object moving through the fluid.
The drag increases with velocity, and there is a terminal velocity
beyond which an object doesn't accelerate further.
Is there anyone who has experimented with a roller-conveyor and can tell us
more about this? In particular, terminal velocity should depend on weight.
As for the proposed national sales tax, on
April 15 I asked what would
happen to people who saved for retirement, paying income tax as they did so;
would they be taxed again on the same money when they spent it to buy things?
Congressman John Linder
has replied to my question.
He says that the actual cost of goods and services - including sales tax - will not
increase under the proposed plan, because the 23% sales tax will be offset by a
comparable reduction in other costs that are presently passed on to consumers
by businesses.
Remember that the cost of a tax isn't just the money it brings in; it's also
the work we are compelled to do in order to fill out tax returns, keep detailed records,
make withholding payments, and so forth.
The income tax imposes this burden on everybody, including all businesses.
The sales tax would impose a burden only on retailers, and it would be a less
complicated burden.
And the purpose of the sales tax is not to increase our taxes, but merely to
rearrange them in way that will reduce hidden costs.
I would like to know whether economists agree with this analysis.
In principle, I think the fairest way to collect taxes is at the point
of spending, not earning.
But I also don't want to squeeze people who have spent their lives
preparing for retirement under the old system, and who aren't prepared for
sudden changes.
|
 |
2004
May
23
|
Feminism that isn't
I have a vested interest in women's rights because
100% of my descendants and 50% of my ancestors are female.
(If 50% of your ancestors aren't, I'd like to know where you're from.)
And I've noticed that today's cultural and political scene contains a
considerable amount of anti-feminism disguised as feminism.
That is, there are people who say they're for equal rights
and actually work against equal rights.
The slippery slope runs roughly as follows:
(1) Women can do what men can do.
(2) Women need encouragement to develop their abilities.
(3) Women need a special, encouraging environment.
(4) Women shouldn't be expected to function outside this special environment.
(5) Women shouldn't be expected to do what men do.
(6) Women can't do what men can do.
Thought I haven't read her books, I understand that a similar critique is made by
Christina Hoff Sommers,
who distinguishes sharply between
equal-rights feminism and the kind of feminism
that is concerned with "reinventing gender" and creating
"feminist" varieties of art, science, mathematics, etc.
Personally, to me, "feminist science" sounds almost as silly as the pink typewriters
and pink automobiles that were marketed to women in the 1950s.
The point of scientific method, like the point of a typewriter,
is to work the same no matter who is using it.
(Admittedly, science should not have masculine cultural trappings needlessly
inserted into it, and I'll certainly listen to critics who want to correct this.)
Analogous things happen to ethnic minorities and disadvantaged groups of all kinds.
When people say they're doing something "for" a minority, make sure
they're not setting up a path into segregation and permanent inferiority.
All too often, the minority embraces such moves willingly because they seem
advantageous in the short run.
I worry, for example, about the African-American student centers that are popping up
in universities: are they signs of respect for a culture, or are they the beginning
of a new segregationism?
By the way, my daughters and I despise "software for girls," i.e.,
inane computer games marketed in pink boxes
with the implication that girls shouldn't like other software and shouldn't like anything
that's not pink.
Software is just software. You don't have to have a Y chromosome to use it.
One more afterthought.
Equal rights do not depend on statistical equality.
To justify giving members of different groups
the equal right to try something,
you do not have to make their statistical success rates equal,
or prove that their abilities are statistically equal.
We know this about sports; why don't we know it about anything else?
|
 |
2004
May
22
|
More about C / Winning against spam /
"Some files can harm your computer"
More about the evils of C and C++: I should add that for the most part, I don't
have anything against the syntax of these languages.
They express algorithms clearly and concisely.
The fall-through behavior of the
switch statement smells of Fortran to me, but apart from that,
it's a nice language, and Java and C# have kept most of the syntax.
The problem is that C and C++ are too low-level.
To use C effectively and stay out of its numerous pitfalls, you have to
think in machine language.
For example, in C, a character string isn't a data type; it's a series of bytes
with characters in them, ending with a zero.
And an array subscript is not just a numbered location; it's an arithmetical operation
on a memory address.
In short, C isn't an algorithmic language, it's a structured assembler.
As a portable assembly language, it was a great idea.
But I often feel that it's the kind of thing that should be the output of a compiler,
rather than the input!
As for C++, it's an improvised object-oriented system on top of (not replacing) C.
That makes an odd mixture.
And C++ is an excessively big language.
One could remark that if there are three ways to do something,
all five of them will be in the C++ Library.
We may be winning the war against spam.
Jeff Duntemann,
who collects and studies the stuff, reported on May 18 that the influx continues to drop.
The FBI is reportedly
planning
to prosecute about 50 spammers later this year
for fraud and for violating the CAN-SPAM Act.
In my experience, spammers and other computer pests can't deal with the concept of
getting punished next year for what you did this year.
They live only in the present, and they feel that if they've gotten away with something
for a week, it's totally behind them. So I expect the trials to be interesting.
In the same news story, a spammer whines that if he labels his ads truthfully as
required by law, AOL won't deliver them.
"Well, duh!" as they say on TV.
That's the point!
You can't force people to receive, at their own expense, ads that they don't want to receive.
The main effect of CAN-SPAM will be to make it easy to block out spam.
Finally, Microsoft and others may actually give us the
long-awaited reform of e-mail technology
so that false addresses will be much harder to use.
Problem: You get an error message box beginning with:
Some files can harm your computer...
when you click on a program or script that is located on another server on your local-area network.
Solution: This is because of the Internet Explorer Security Enhancements in Windows Server 2003.
Windows is trying to keep you from being tricked into running something from a web site.
Even though you're not using your web browser, the same security tests are performed when you
click on files directly or through shortcuts.
To prevent the error message, open Internet Explorer and choose Tools, Internet Options, Security.
You'll probably find that Local Intranet is selected. Choose Sites and add the server that holds
the programs you want to run. If you type \\server1, it will go into the list as
file://server1; that's normal.
Comment: Curiously, "Local Intranet" does not automatically include your
workgroup or domain. Perhaps it should.
|
 |
2004
May
21
|
What's wrong with software as we know it
Let me expand on a point made by
Jeff Duntemann
in his entry for May 20:
Most of what's wrong with software as we know it
(the unreliability, and especially the security holes)
is due to the C and C++ programming languages
(in which UNIX, Windows, and most commercial software products are written).
These languages have two serious flaws.
- Buffer overruns: The standard C and C++ routines for inputting character strings
(i.e., almost any kind of information) require the programmer to set aside a specific amount
of memory (a "buffer") to hold the incoming data, and
there is no checking whether the data will fit.
Excess data just overwrites whatever is stored in the subsequent memory positions,
usually part of the program itself.
At best, this just crashes the program, either immediately, or later, when
the overwritten code is executed.
And of course the crash is unpredictable and irreproducible.
More seriously, though, buffer overruns create security holes.
Vandals use them to put their own code into memory in place of the executing program,
even through a network connection.
That's how they gain control of a computer and break into it.
I see people try to do this with my HTTP and FTP servers every day.
I've installed extra protection, so I catch them doing it.
- Uninitialized pointers: A pointer is a memory location that stores the address of another
memory location. This leads to powerful techniques, but it's the kind of thing
the programming language should do for you. Lisp and Prolog are highly pointer-based,
and they do all the pointer manipulation for you.
In C and C++, there's no checking whether a pointer contains a valid address.
So it's easy for a program to do things that are entirely unexpected and irreproducible.
Irreproducible because the contents of an uninitialized memory location will depend on
whatever was there previously, when another program was running.
There's no reason a computer program can't set all its memory locations to something
predictable (such as zeroes) before using them. But C and C++ don't do this.
Why not use C#, Java, or another language that protects you from these hazards?
Because C programmers are macho. They like to ride without a helmet, so to speak.
They will tell you that if the computer checks for buffer overruns or uninitialized memory,
it will be intolerably slow.
Computers are 1000 times as fast as when C came out, and we still don't have time for
some automatic checking? Time for a reality check, folks!
Most people would gladly accept software that's 5% or 10% slower
if it's ten times as reliable!
I'll come right out and say it: in my opinion,
the C language was a technological setback when it came out in the late 1970s,
because better-designed languages (such as Algol 68 and Algol W) already existed.
C's kluged object-oriented extension, C++, was even worse.
C was designed to be fast, easy to implement, and nothing else.
It got its simplicity from leaving out nearly
everything that could protect you from your own errors.
Update: For a partial (but only partial!) retraction of these remarks see
July 8, 2008.
You'll notice that there's a
Google search bar at the bottom of this page, and
also on my Previous Months page.
This is a free service from Google and does not require registering with them.
To get one for your web site,
here.
All you have to do is copy their code and put your domain name into it.
Adept HTML programmers can customize it a bit, but you have to display
the Google logo as part of the terms of service.
Our latest local controversy - or maybe I should say stink - is the
Watkinsville
chicken manure caper.
Make of this what you will...
|
 |
2004
May
20
|
Too busy
I'm too busy to write anything today, but yesterday I
rewrote most of
this.
Now you know a little of what I do for a living.
Next, it's time to dive deep into some research projects that are under nondisclosure.
|
 |
2004
May
19
|
Sigh of relief / A-life pets / Interesting new online Bible
At last! Interland's nameserver problem has been corrected, and the entire world
should again be able to reach covingtoninnovations.com without difficulty.
Bring 'em on!
 Cathy's new web site, alifepets.info,
is up and running, though not complete.
Cathy's new web site, alifepets.info,
is up and running, though not complete.
"A-life" stands for "artificial life," the realistic simulation of living things.
A-life pets are games in which you take care of simulated pets.
These range from the Tamagotchi and Furby of a few years ago, all the way up
to elaborate horse-breeding simulations.
All the fun of the real animals, and none of the mess!
Cathy also has a site,
magnoliapetz.com,
devoted to one particular group of games (Petz, with which the picture at the right was generated),
and back in eighth grade, she won a science fair grand prize with a pet simulation program of
her own called Dotts.
But today, she's busy learning linear algebra and graphics algorithms
in a special summer program
here.
Congratulations, Cathy!
Yesterday I came across
an interesting new Bible translation
that happens to be available on line, as hypertext.
I'm referring to the
Holman Christian Standard Bible
(CSB).
As a churchgoer who is also a linguist and knows Hebrew and Greek, I'm expected to know something
about Bible translations, so I'll be keeping my eye on this one.
Its goal is apparently to clear up controversies
raised by a number of recent, competing translations
by giving
unusually detailed footnotes about the range of possible translations
of difficult words.
The web page describing the
translation is here.
One brief but useful critical review of the CSB is
here.
It's part of a set of reviews of different translations.
One particular hot-spot is the treatment of gender in language.
If a Bible translator says man or he where the original
text didn't, there will be trouble.
This happened in 1 Thessalonians 3:10, rendered by the New International Version (NIV) as,
"If a man will not work, he shall not eat" - but the original Greek doesn't say man,
and "Whoever will not work shall not eat" (NRSV) is a much more accurate translation.
I could imagine somebody reading the mistranslation and preaching a sermon about how only
men are expected to work.
Despite that fumble, the NIV is generally quite good.
A recent attempt to make it fairer, the TNIV, fumbled badly in numerous places
(even mixing up singulars and plurals),
and the CSB apparently arose partly as a reaction against it.
But accurate handling of genders in the Bible
is hard because Hebrew and Greek are radically different from English,
and if you aim for complete neutrality, you often get clumsy English
(which is mistranslation of a different kind).
For much more about this, click
here
and go to page 21.
I'm not sure we really needed another Bible translation,
but the footnotes indicating alternative translations in the CSB will be a real eye-opener for some.
Gone are the days when the ordinary churchgoer or preacher can get away with
equating King James' English with the Word of God.
The Bible is written in human languages - which happen not to be English - and in order
to understand it, you have to know how human languages work.
|
 |
2004
May
18
|
Another deluded nameserver
("I don't know, but I'm the authority!")
[The problem described below was corrected on May 19.]
This is what it looks like when a nameserver
doesn't know where you are, but still claims to be authoritative for your site:
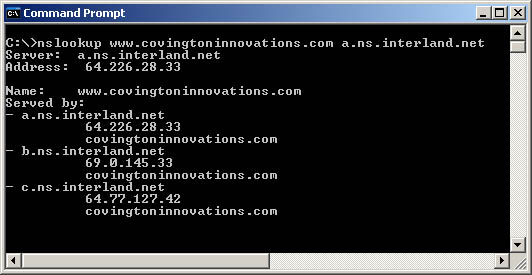
I used the nslookup command to ask Interland's primary nameserver (a.ns.interland.net)
where to find www.covingtoninnovations.com.
Here's the answer I got: "I don't know, but the authoritative nameservers are
a.ns.interland.net,
b.ns.interland.net, and
c.ns.interland.net."
But these aren't the authoritative nameservers for this domain.
They were changed last Saturday (May 7).
I'm trying to get Interland to correct this problem.
Any number of computers may still be taking Interland's word that my site doesn't exist.
|
 |
2004
May
17
|
Using the hosts file in Windows
UNIX sysadmins are familiar with a file called /etc/hosts.
Well, Windows has the same file.
Under Windows 2000/XP/2003, it is
%windir%\system32\drivers\etc\hosts
where %windir% evaluates to either C:\windows or C:\winnt.
The hosts file gives you a way to associate names with IP addresses.
It takes priority over the nameserver system, so in the hosts file,
what you say goes.
The computer will use the definitions given there and ignore all other
definitions of the same addresses.
The hosts file is plain ASCII text, editable with Notepad.
If you put into it the line
216.89.218.227 www.covingtoninnovations.com
then your computer will always resolve www.covingtoninnovations.com
to 216.89.218.227, regardless of what any
confused nameserver may tell it.
This means that the hosts file has four main uses:
- To identify domain names that may be missing or incorrect, or just take too
long to look up in the nameserver system, as in the example just given.
- To give handy nicknames to sites that aren't nameserved, or whose names are
hard to remember.
For example, my router is addressed as 192.168.1.1 from within my home LAN.
I have trouble remembering this number, so in my hosts file I've added:
192.168.1.1 router
so I can get to its Web interface as http://router.
- To map names to numbers for a LAN reached by VPN. Recall that
couple of days ago,
I noted that one of the machines on my VPN had to be addressed by number
because it had two Ethernet cards and the nameservers would direct it to the wrong one.
Not if I put it in my hosts file!
The requisite entry is something like:
192.168.98.98 server2
(pretending that those are its name and IP number, which they aren't).
This guarantees that \\server2 will map to that number.
I've actually done this for all the computers that I commonly reach by VPN,
not just the one that isn't nameserved.
The reason is that this gives me much quicker access.
The time taken to look up a server name on a VPN can be as much as half a minute
on the first try (much slower than Internet nameserving).
- To block access to certain sites in a somewhat clumsy way.
If you map a site to a nonexistent address, such as:
10.100.101.102 www.covingtoninnovations.com
then users of your machine will not be able to go to www.covingtoninnovations.com by name,
either directly or by following links from other pages.
They can still go to it by number, so you haven't really blocked it out.
I chose 10.100.101.102 as a nonexistent address because all IP numbers beginning with 10
are reserved for use within local area networks (not the Internet). Unless your LAN is
truly gigantic, or somebody just decided that 10.100.101.102 would be a good number to use,
that number is not going to be in use. And even if it's in use, it won't
be www.covingtoninnovations.com.
Editing the hosts file requires administrator privileges.
However, you do not have to reboot or restart anything after editing it;
its effect is immediate.
|
 |
2004
May
16
|
Rattie Palace / Dueling nameservers reconciled
 One of the most amusing pieces of woodworking ever to grace our home
left us today.
The "Rattie Palace," former home of Cathy's pet
rats,
has been donated to the
Athens Humane Society,
where it's going to be the home of some
domesticated rats if their unofficial receptionist (a cat)
doesn't take possession of it first.
One of the most amusing pieces of woodworking ever to grace our home
left us today.
The "Rattie Palace," former home of Cathy's pet
rats,
has been donated to the
Athens Humane Society,
where it's going to be the home of some
domesticated rats if their unofficial receptionist (a cat)
doesn't take possession of it first.
The Rattie Palace was built by Melody's father, who enjoys whimsical woodworking projects.
It includes a pendulum, ramps, spaces for hammocks, and a tube down which food can be dropped.
Rats make surprisingly good pets.
They are like kittens that never grow up.
Most of the mice you have seen in children's cartoons are actually rats, to judge by their behavior.
They are social animals, very solicitous of each other, and they trust humans much more than any cat ever did.
Usually, if removed from their cage, they want to get back into it - after having an adventure first, of course!
The last surviving pet rat, Charles, now lives in a 10-gallon tank and thinks he's human.
He is about to celebrate his third birthday, which makes him a very elderly rodent.
[Note added 2004 May 17:] The following problem has been corrected.
A nameserver that was not updating properly has been found and fixed.
Reading about it is still instructive, though.
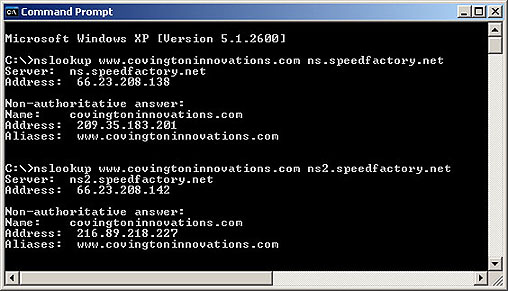 Today Speedfactory's two nameservers disagree as to where I am.
The second one is correct.
Today Speedfactory's two nameservers disagree as to where I am.
The second one is correct.
Things like this are why
a substantial number of people still can't reach me
by Web or e-mail.
I am not sure it is Speedfactory's problem. It has been hard to get Interland
to stop claiming to be authoritative for covingtoninnovations.com
(which they ceased to be 8 days ago),
and Speedfactory is located in Atlanta, near Interland.
There is a similar disagreement about where to deliver my mail, as revealed by
the command:
nslookup -type=mx covingtoninnovations.com server
Just to keep the dramatis personae straight:
Speedfactory provides
the DSL line into my house;
Sectorlink hosts my web
pages and e-mail, as of just now;
Interland used to host my
web pages and e-mail, but they're too expensive for a small site like mine.
|
 |
2004
May
15
|
Comics, VPN, and other strange adventures
If you liked The Far Side when it was on the comic pages a few years ago,
you'll probably like
Speed Bump, which I just found on the Web.
(Today's panel is not one of the best; skip to a different day for a better sample.)
Enjoy!
[Minor revisions 2004 May 16, 17.]
Virtual Private Networking (VPN) is a way to establish a safe, encrypted communication path
across the Internet to a particular server that recognizes you as an authenticated user.
VPN has two main uses:
- Remote access, so you can get to shared files and printers on the server from
your remote location;
- Routing, so you can get into the whole LAN at your office from your home.
Until now, we were doing the first of these, and on a Windows server, it's relatively easy to set up.
Choose Administrative Tools, Remote Routing and Access Server, and follow the instructions.
The second is harder. Doing both of them together is harder yet.
I won't explain the whole process, but the key idea is you have to have two Ethernet cards
in the server even if they are both connected to the same network.
VPN routing is so set on the idea of connecting two separate networks safely that
you have to have two cards even if the two networks are the same.
You also have to set the VPN server to give out IP addresses that are in the same range
as you use locally on the LAN so they will be recognized by the LAN.
And you may have to get into the server by IP number (e.g., \\192.168.111.234\foldername).
To get into the server, use the IP number of its second Ethernet card (the one that it
considers to be its LAN connection).
If you try to get into it by name, you'll probably get the wrong Ethernet card.
You can get into all the other computers on the LAN by name in the normal manner.
[Note added May 17: You can get around this problem by editing the hosts
file. I suggest putting several of your most-used LAN servers in the hosts file, not
just the one you absolutely have to address by number. It speeds things up.
Thanks to Martijn Middelplats for this information.]
I have no further advice about this labyrinthine business, so please don't e-mail me with
questions. But see
Microsoft's wordy documentation
and
ChicagoTech's clear and helpful support pages.
Regarding the origin of the term ham radio (mentioned yesterday),
I should add that I've heard the story about H. A. M. being the initials of the names of 3 ships.
But I don't believe it. There's no evidence that it actually happened.
In fact, the story itself disturbs me.
Do some people think that the history of a word is something you get to make up, just
to see if anyone will believe your story?
We're talking about history and real events here, folks.
Last night Comet NEAT passed next to the star cluster M44 in Cancer.
It was a fine sight, but the sky clouded up before I could take a picture.
Also, right then
I had to run to the lab because, working from home and trying to set up VPN,
I inadvertently took our server off the Internet!
|
 |
2004
May
14
|
This is not an A.C.R.O.N.Y.M.
One of my pet peeves - and I have many - is the way some people think some words
are acronyms (abbreviations) when they are not.
One of my hobbies is ham radio. Not HAM radio. Certainly not H.A.M. radio.
"Ham" is not an abbreviation.
It's derived from "ham actor," which in turn alluded to some old minstrel shows
that are best forgotten. The reason ham actors got associated with radio is that
the very first radio experimenters were allowed to broadcast entertainment to
the public - amateur entertainment, of course. Not any more, but the name stuck.
And unsolicited commercial e-mail is spam, not SPAM or S.P.A.M.
The corresponding brand of canned meat
is called SPAM on
Hormel's web site,
because all of Hormel's trademarks are written in all capitals there
(a practice also followed by Kodak and other companies).
The name is derived from spiced ham, not (as folklore sometimes says)
Specially Processed American Meat, so the letters SPAM
are not an abbreviation and don't need to be in all caps.
And the name of our university can be abbreviated U.Ga., or UGa if you don't
have punctuation, or UGA if you don't even have lowercase letters.
But not U.G.A., which would imply that U, G, and A stand for three words.
"University of Georgia Aaaaaah-what?"
Not "University of Georgia at Athens," because that is not its name;
alert Georgians are well aware that there is no University of Georgia in Atlanta
or Homerville or Pavo or anywhere else.
Worst of all are PEOPLE WHO THINK EVERYTHING ON A COMPUTER HAS TO BE IN CAPITAL LETTERS.
I wonder if they are posting their e-mail with a vintage 1958 card punch!
|
 |
2004
May
13
|
DNS woes
Sadly, Interland didn't stop nameserving my old accounts until the exact moment they
took them down, which was sooner than I expected.
A more orderly process would have been to stop nameserving as soon as they ceased to be
authoritative for the domain name (last Saturday) but leave the accounts open
for about three days while computers around the world were finding out about the move.
So there are people out there who still can't reach me by Web or e-mail.
If you are reading this, you aren't one of them!
Friday the 13th came on Thursday this month...
|
 |
2004
May
12
|
Comet NEAT / My epitaph

Here's a picture of
Comet NEAT
from some time at the end of last week.
This was taken with a Nikon camera body and 180-mm f/2.8 telephoto lens
"piggybacked" on a Celestron 5 telescope to track the earth's motion.
The exposure was probably about 5 minutes on Ektachrome E100GX film pushed 1 stop.
Exact details, as well as date and time, are buried in my notes somewhere.
This will appear in my
gallery
later, with full details.
As some of you have found out the hard way, we've moved.
Slightly to my surprise, Interland cancelled my old account within
about 2 hours of my requesting it (they had said to give 48 hours' notice).
Some sites, including my home, are still being nameserved the old location
and are getting an error message.
Oh, well; if you're reading this, you've found it...
Today was a very busy day moving user accounts to a new server in the AI Lab,
as well as dealing with a security incident (about which my lips are sealed)
and a minor hardware failure (thank goodness for RAID).
But I've decided what I want on my tombstone:
the words that I so often utter to people around me,
namely:
| WHAT DID THE ERROR MESSAGE SAY? |
If you've ever done computer support, you know exactly what I'm talking about!
|
 |
2004
May
11
|
Miscellany
Almost everybody is now reading this column on my
new host at Sectorlink
rather than the old one at Interland.
If the logo at the upper right corner of this page includes the words OLD SERVER,
you're one of the unfortunate few.
Today's is in fact the last column that I'll upload in both places. After that, I'll do
a few tricks with redirection to handle the stragglers
(the people whose nameservers aren't up to date).
 One of my most notorious exploits - pardon me, I mean one of my
most successful projects - is a
book about astrophotography
first published in 1985 and last revised in 1999.
I maintain a comprehensive page of updates for this book on its
web page and have just added a
quick checklist
of what's changed since the 1999 edition came out.
One of my most notorious exploits - pardon me, I mean one of my
most successful projects - is a
book about astrophotography
first published in 1985 and last revised in 1999.
I maintain a comprehensive page of updates for this book on its
web page and have just added a
quick checklist
of what's changed since the 1999 edition came out.
Computer virus authors are
getting caught,
thank goodness!
Computer virus authorship is, in my opinion, a much worse crime than bank robbery
because the bank robber generally has a use for the money;
the virus author just wants to cause harm.
Future generations will look back on 1993-2003 as
the time when society lacked the will to stop computer crime
and simply hid its head in the sand.
For nearly a decade, governments viewed viruses and spam as
mere disputes between computer hobbyists.
All of this will seem surreal when we look back on it.
I do have a few educated guesses about the German virus author who has just been arrested.
Bear in mind that all I know is what I read in the papers and I can only guess
that he is typical. Based on that assumption, here's what I think:
- He probably thinks he's a great programmer when in fact he is only moderately competent.
He's probably adept at reading machine language code
and following instructions received from others.
He's probably not the kind of person who will ever invent anything significant.
- He probably feels superior to most of humanity.
The term is "elite hacker."
Many people - even the people who run some large organizations - feel, deep down,
that computer experts are superior human beings who ought to be exempt from society's rules.
They're (we're) not.
- He probably lives in a half-fantasy world with a remarkable amount of
doublethink about whether his creations will actually harm people.
To the typical computer criminal, the Internet is a huge video game, and the
people on the other end aren't really people. They're just pawns in a game.
- He almost certainly intended to do tremendous harm with his computer
viruses, even though he will surely deny it.
The most spooky thing about criminology is that guilty people are almost always
innocent in their own eyes. (Ask any prison chaplain.)
- He blames the victims for the harm they suffered.
This was a constant theme when I was investigating computer crimes for the
University of Georgia.
The perpetrators always claimed that if you didn't have the latest, most unpickable locks,
it was your fault that you got cracked.
They had never realized that
in the real world, we do not make crime physically impossible.
We often make it mildly difficult, but we aren't expected
to make our buildings completely impenetrable in order to
keep out burglars.
The real purpose of locks is merely to
distinguish burglary from normal use of the door.
- He doesn't expect to be punished because of his youth and his
superior status; indeed, he didn't even think he could get caught.
Those are just educated guesses.
Already another virus author has also been arrested, and we'll see how the story
plays out.
Apparently, most of the viruses of the past year are the work of very few people.
|
 |
2004
May
10
|
Spelling, punctuation, and heckling TV shows
Why bother to spell and punctuate correctly?
Because, fundamentally, it's a matter of politeness.
An important step toward maturity is achieved when a person realizes that
the audience is more important than the writer.
If you want to entertain and influence me,
you should want to produce something I'll enjoy reading,
rather than demanding that I decipher your idiosyncratic scratchings.
This point is made eloquently in, of all places,
the FAQ file for Television Without Pity,
a web site devoted to heckling TV shows.
(Scroll down to the second question on the page.)
And while you're at it, have a look at
the rest of the site and
enjoy incisive criticism of stupid TV shows!
|
 |
2004
May
9
|
Easier than moving a cemetery
 I've moved covingtoninnovations.com from
Interland in Atlanta
to
Sectorlink in Michigan.
My new monthly fee (for web hosting and e-mail but not network access) is $10
rather than $25, and Sectorlink's technicians answer questions almost instantly.
I've moved covingtoninnovations.com from
Interland in Atlanta
to
Sectorlink in Michigan.
My new monthly fee (for web hosting and e-mail but not network access) is $10
rather than $25, and Sectorlink's technicians answer questions almost instantly.
But you are probably still looking at this page on the Interland site.
(To check, look for the words "OLD SERVER" in the Covington Innovations logo
at the upper right corner of this page.)
The reason is that it takes 3 days for the change to propagate through
the domain name server (DNS) system.
Name servers are the computers that tell your computer where
covingtoninnovations.com is located.
More precisely, they tell it what IP number corresponds to covingtoninnovations.com.
It used to be 209.35.183.201;
now it's 216.89.218.227.
Today my new host, Sectorlink, told my domain registrar,
Network Solutions,
that the new name server (ns10.servdns.com) is authoritative for my domain.
Thus, any sufficiently curious computer can now look up covingtoninnovations.com
and get the new IP number.
But computers don't normally query the authoritative name server for each domain;
that would be too much work.
Instead, they query the nearest name server that thinks it knows.
So at any given time,
most of the DNS system is still using information that it cached some time
during the previous three days. And that's why the change hasn't "taken" yet.
I get e-mail at covingtoninnovations.com as well as hosting web pages.
So here's what the whole moving process is like:
(1) Open the new account. (Done.)
(2) Upload a copy of all the web pages to the new account. (Done, but I'm still dealing
with minor problems and discrepancies.)
(3) Create e-mail accounts on the new account corresponding to those on the old account. (Done.)
(4) Notify the domain registrar that I've moved. (Sectorlink has done this for me.)
(5) For a few days, maintain current web content and check e-mail
on both sites, because different computers will be
accessing either one, unpredictably. (I'm doing that now.)
(6) On May 15, close the old account, leaving in place a web page that says, "We've moved,"
which will last only until Interland cleans up their disks.
So that's what I'm up to...
It's a lot easier than moving a cemetery, though perhaps not radically different in nature!
Happy Mother's Day, Melody!
|
 |
2004
May
8
|
How many bad ideas can you spot here?
A nearby newspaper - which I won't name because I'm still trying to persuade its
publisher to change his mind - has decided to
require its readers to register to read the online edition.
Not pay, just register.
Many newspapers require readers to provide a unique identifier, such as an
e-mail address and password, in order to read the news.
I find this annoying.
But this newspaper is proposing a particularly ill-conceived version of the scheme.
They want my name, address, telephone number, date of birth,
gender, and permission to send me advertising by e-mail!
And they tell me to set my browser to "accept all cookies."
All of this strikes me as a really bad idea for
numerous reasons. Here are some of them...
-
Why should I give them personal information that could lead to identity theft?
I can understand filling out a demographic survey, but must they have my
address, telephone number, and exact date of birth?
Particularly the date of birth - it's something you can't look up in directories,
so it would help a thief impersonate me.
A basic principle of information security is,
don't give out private information unnecessarily.
-
What makes them believe they will get accurate information?
How will they know I'm using my own name and address, and not somebody else's,
or a totally nonsensical one?
People are already doing this to other newspapers.
I suspect they're about to get a huge database of nonexistent people.
-
Why are they telling us to make our browsers insecure?
"Accept all cookies" may be convenient for them, but many
of us think it's not safe for us.
If your browser accepts cookies indiscriminately,
sooner or later you'll end up with spyware.
-
Why should I consent to receive e-mailed ads?
If you know anything at all about the Internet, you know that
people hate receiving advertisements by e-mail.
We're drowning in a sea of unwelcome advertising.
-
What makes them think we will receive their e-mailed ads?
Have they never heard of spam filtering?
-
Why don't they want me to refer people to their newspaper?
Lots of people like me write blogs or other web pages on which they mention news stories.
Now I won't be able to link to their newspaper, because unregistered people
won't be able to follow the links.
Why is this good? For whom?
-
Why don't they want everybody to read their paper and see the ads?
The advertisers supposedly want the readers to be registered.
I fail to see why.
If I were an advertiser, I'd want my ads to be seen by
every potentially interested person in the world.
Blocking anyone out is stupid.
-
Why don't they realize it's rude?
People are offended when personal information is gathered about them unnecessarily.
Do you remember when Radio Shack used to ask everyone their telephone numbers?
Do you remember, also, that under strong pressure from the public,
Radio Shack abandoned this practice?
Asking too many prying questions is a great way to make yourself unpopular.
If what the advertisers want is to know how many people are viewing the ads,
they can count the IP addresses from which the web pages are retrieved.
No birthdays, no telephone numbers,
no reducing the reader's computer security,
no cooperation requested from the unwilling victim.
What could be more straightforward?
As it is, it sounds like this newspaper is trying to drive away most of its online audience
for no good reason.
|
 |
2004
May
7
|
Still more speakers
 Yesterday Melody's car, our 1995 Dodge Caravan, got new speakers fore and aft.
In the front we put Sony XS-R1311 speakers (5 1/4 inch, 3-way, 35 watts continuous).
These are apparently a "Wal-Mart model" quite similar to the
XS-V1330A
depicted here, but with slightly less power capacity.
Yesterday Melody's car, our 1995 Dodge Caravan, got new speakers fore and aft.
In the front we put Sony XS-R1311 speakers (5 1/4 inch, 3-way, 35 watts continuous).
These are apparently a "Wal-Mart model" quite similar to the
XS-V1330A
depicted here, but with slightly less power capacity.
By "Wal-Mart model" I mean a model sold only at Wal-Mart.
Because Wal-Mart insists on the lowest possible wholesale prices,
many manufacturers make special versions of their products just for Wal-Mart,
so they can't be accused
of giving someone else a lower price on the same item.
There was even a Wal-Mart model of the Meade ETX-125 telescope, with MA instead
of Plössl eyepieces.
Installing the front speakers was a snap - literally. The appropriate part of the dashboard
simply pries up; gentle pressure releases about a dozen clips that hold it in place.
Lift it up, change the speakers (there's plenty of room for protruding tweeters), and
put it back down.
The only reason the job took 30 minutes was my old-fashioned insistence on soldering the wires.
A modern installer would have used crimp connectors.
That sounded so good that we decided to upgrade the back also.
Those who keep up with such things will know that not all 6×9 speakers fit the
rear liftgate of a Dodge Caravan or Plymouth Voyager.
There isn't much room for a protruding tweeter.
 After much agony, we bought a pair of
Pioneer TS-G970M 4-way speakers
(apparently another
Wal-Mart model, similar to the
TS-A930P
with a supertweeter added)
and resolved to make them fit.
To our surprise nothing had to be cut.
They just fit in the space available.
If the tweeters had protruded just a little further - like the competing Sony product -
we would have had to cut something.
After much agony, we bought a pair of
Pioneer TS-G970M 4-way speakers
(apparently another
Wal-Mart model, similar to the
TS-A930P
with a supertweeter added)
and resolved to make them fit.
To our surprise nothing had to be cut.
They just fit in the space available.
If the tweeters had protruded just a little further - like the competing Sony product -
we would have had to cut something.
And they sound great! Why didn't we do this years ago?
Admittedly, the original rear speakers weren't as cheaply made as the ones in the Oldsmobile.
Chrysler had given us dual-cone (but 1-way) 4-ohm speakers in the rear,
so at least they were already a good electrical match to the Sony receiver.
Comet
NEAT is now passing through a field of star clusters (M47 and environs).
It is a fine sight in binoculars, much higher in the evening sky than before.
It is to the upper left of Sirius.
It's the last day of the semester and tomorrow I disappear under a pile of papers to grade!
More news when I emerge...
|
 |
2004
May
6
|
Decline of spam? / More about music
Jeff Duntemann reports
a 40% decline in the amount of incoming spam during the past couple of
weeks.
What has gone away is mostly the spam that was being re-sent from virus-infected computers.
To elude detection, many spammers don't send out their own ads; instead,
they release viruses that will cause the ads to be sent from the victims'
computers. That kind of spam has dwindled.
What's going on?
It may be the recent arrests of spammers under a
newly passed law.
(Either the arrested spammers were themselves responsible for 40% of the problem - which
just might be possible - or the arrests have deterred others.)
Or it may be that Microsoft's latest security patches have blocked these particular viruses.
One of the interesting things you can do on
Amazon.com
is listen to samples of music CDs and thereby
compare different performances of the same music.
With this in mind, last night I went looking for instrumental performances of songs
by Simon and Garfunkel.
I contend that their songs need to be played almost like baroque music, with
precise timing and clear separation between different instruments, since there are
lots of contrapuntal effects, with multiple tunes interacting.
"Scarborough Fair/Canticle" is the most obvious of these, but there are others.
Compare the crisp
London Pops
rendition of "Homeward Bound"
(in which the instruments practically talk to each other)
with
this
mushy one, which runs everything together and has sloppy timing.
I must be the only person who, as a teenager in the 1970s, knew Simon and Garfunkel's music
in instrumental form long before hearing most of the lyrics.
(Details here;
maybe you can help me identify an obscure album...)
So I came to appreciate the rather elaborate and evocative tunes for their own sake.
In fact, my first reaction to the words of "Homeward Bound" was,
"Yes; the words say exactly what the tune says; but the tune says it better without the words."
See the corrections
to my May 2 item about the background of the Windows logon screen.
|
 |
2004
May
5
|
More advertising follies / A tale of two speakers
This morning, I was reading
this
CNN news story about schoolteachers who defrauded their employers with fake postgraduate degrees.
And in the advertising column on the same page, I saw ads for "realistic replica diplomas" and
mail-order degrees.
Obviously, these ads came up automatically because "diploma" occurred in the news story.
They rotate; when I came back to the page I saw different ads.
But it certainly gives the impression that somebody at CNN either approves of the fraud or
just isn't paying attention!
By the way - as our worst students sometimes ask - who is the victim when you cheat in school?
The trite answer is, "You're cheating yourself," but that's not correct.
The true victim of any kind of academic fraud is the employer or client who is relying on you
to have a genuine degree.
Cheating on even one test makes your degree partly fake.
It recently came to my attention that I listen to music in my car and,
nowadays, not much of anywhere else.
When I was single, I listened to a lot of music at home, but as soon as my children
were born, I always preferred to be able to hear what else was going on in the house.
And that preference has never left me.
Anyhow, I realized that an upgrade to the car stereo might be in order.
I should explain that the car is a 1996 Oldsmobile; I don't consider a car
well-broken-in until it has 60,000 miles on it, and if it's not good for 15 years
of daily use, it's just not a good car!
So I plan to keep this one until at least 2011.
A few years ago Melody and the girls surprised me by replacing the original radio
with a Sony receiver, 40 watts × 4 channels (left, right, front, back).
Soon afterward I replaced the tinny 3.5-inch front speakers with
Infinity 3002cf
2-way speaker systems; that really helped.
But the sound still had a shrill quality, presumably because of the speakers'
small diameter.
 So yesterday I had the rear speakers replaced with
Sony XS-V6935X
3-way systems
(depicted here with Sony's permission).
So yesterday I had the rear speakers replaced with
Sony XS-V6935X
3-way systems
(depicted here with Sony's permission).
Dramatic improvement! With about 75% of the signal sent to the rear speakers,
the music seems to come from nowhere; that is, I'm listening to an orchestra rather
than a speaker system.
I had been especially
bothered by the violins in the first movement of Vivaldi's Four Seasons
(Israel Philharmonic recording).
In the front speakers, they were screechy; in the rear speakers, muffled.
Now they sound like violins.
But I think I prefer the performance by the
English Chamber Orchestra (with H. Szeryng, now out of print);
it seems to have had a better microphone setup.
Fortunately, the rather theatrical-looking silver-colored grille frames are not needed; the new
speakers mount in place of the old ones and are
not visible from the outside.
I'm plotting what I might do with the new grille frames and the old speakers...
I could make something that sounds as dreadful as it looks!
The old speakers, by the way, were miserable.
They sounded muffled, and now I know why.
On inspection, they turned out to be
single-cone speakers similar to those used with 1960s car radios
(when a "rear speaker" was the latest luxury).
And their 10-ohm impedance kept the Sony receiver from delivering much power into them.
The moral? Get new speakers when you get a new car stereo, if at all possible.
Next project: to upgrade the speakers in the Dodge Caravan that Melody drives.
It has a similar Sony receiver (installed about 4 years ago) but the speakers
are all original.
|
 |
2004
May
4
|
Comet NEAT
I'm told that Comet NEAT is putting on quite a show low in the southwest after sunset.
It's no Hale-Bopp, but it is reportedly quite easy to see in binoculars.
We're going to look for it tonight, and I'll post an update.
Details are
here;
the best time to look is about 9:00 to 9:30 p.m. (in northern Georgia).
Finding the stars Betelgeuse and Sirius is an important prerequisite.
And I do mean low in the southwest. Get away from the trees; look over water if possible,
or wide, treeless fields.
The best view will actually be tomorrow night (Wednesday);
each evening, the comet will be higher in the sky, but fainter.
The comet was discovered by the Near Earth Asteroid Tracking (NEAT) research project,
hence the name.
Note added 11:15 p.m.: Several people have assured me that the comet was a fine
sight last night, but tonight, we could not see it with the unaided eye
(partly because of bright moonlight).
The brightness of any comet is subject to a lot of fluctuation, but it should
still be near its maximum for several more days, and we'll be seeing it against
a darker sky.
Tonight it was a fuzzball, about 3rd magnitude,
with no visible tail.
We were able to see it with 8×40 binoculars.
In coming days, it will be visible against a dark sky and may be more impressive,
at least through binoculars and telescopes.
|
 |
2004
May
3
|
Lost days, thanks to Interland
This morning, this entire web site reverted to the state it had been in on April 30,
and I couldn't do anything about it.
As far as I can determine, my service provider,
Interland,
has not entirely corrected the problem yet,
but at least I can re-upload the files now.
This is not the first time in recent weeks that the whole web site has lost
recent changes and reverted to an earlier state.
This one was particularly bothersome because Sharon was at school,
trying to give a presentation with material she uploaded yesterday,
and it vanished right out from under her.
I think basic ethics requires the provider to notify users when they
knowingly disrupt their data.
I am looking for a new web hosting provider.
|
 |
2004
May
2
|
Windows logon wallpaper
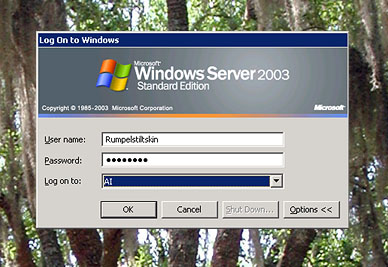 Here is how to control the background that users see while logging onto a
Windows computer, either locally or through Remote Desktop.
Here is how to control the background that users see while logging onto a
Windows computer, either locally or through Remote Desktop.
(1) Create the desired background, as a 1200×1600-pixel, 8-bit indexed-color BMP file.
(2) If there is anything in the background that all users must see - such as the name
of the machine - put it just below center, about 1/3 of the way up from the bottom.
[Corrected May 5.]
Remember that because of varying screen sizes, most people won't see all
of the background.
(3) Store the file in \WINDOWS\SYSTEM32 or \WINNT\SYSTEM32 as the case may be.
(4) Put the file name in the Registry under
HKEY_USERS\.DEFAULT\Control Panel\Desktop
as the value of Wallpaper.
In Windows XP, users won't see this background if Windows is displaying the
Welcome Screen (a menu of user accounts).
To control whether the Welcome Screen is used, use Control Panel, User Accounts.
|
 |
2004
May
1
|
Are there two of you? / Spammers
What happens when a Windows roaming user logs onto two PCs at once?
Recall that with Roaming User Profiles, the user's desktop is copied from the server
to the client PC at logon, then copied back to the server upon logoff.
This implies that if you log onto two PCs, the one that you log off last will win,
and any changes made to the desktop on the other one will not stick.
That's how it was under Windows 2000.
But, as Microsoft explains,
Windows XP merges the desktops rather than overwriting them
to "provide a better user experience."
Good for them.
In our lab,
we provide users with a home directory on a shared
drive (accessed as U:, and containing the My Documents folder).
This resides on the server at all times, with no copying, and is the preferred place
to store one's work.
Apparently, Georgia Tech
has adopted a similar practice.
Can you go to jail for spamming?
Yes,
finally, thank goodness!
Spamming is harassment and theft of services on a gigantic scale.
Never forget that e-mail costs money to receive.
I believe that most of the spam in the world comes from just a few people.
I also believe that the only way to solve the spam problem is to
redesign the e-mail protocol so that forgery and concealment are much
harder.
They'll never be impossible, but right now they're ridiculously easy,
and spammers rely on concealing where their mail is coming from.
If it were possible to send complaints back to the place the spam actually came from,
spamming would be nearly impossible.
Another clever anti-spam tactic is the
Teergrube
(German for "tar pit").
When any server starts receiving spam, the idea is not to merely reject it, but also to
slow down and waste the spammer's time.
Keep him on the line for five minutes for a transaction he expected to complete in half a second.
I hope this works!
As I used to say to spammers when I was handling computer security,
we may not be able to stop you, but
we can inconvenience you to the ends of the earth.
All that's needed is for the good guys to be determined to drive the bad guys crazy.
|
 |





 Yesterday afternoon, on her way to class,
Yesterday afternoon, on her way to class, 


 One of the most amusing pieces of woodworking ever to grace our home
left us today.
The "Rattie Palace," former home of Cathy's pet
One of the most amusing pieces of woodworking ever to grace our home
left us today.
The "Rattie Palace," former home of Cathy's pet
 Today Speedfactory's two nameservers disagree as to where I am.
The second one is correct.
Today Speedfactory's two nameservers disagree as to where I am.
The second one is correct.


 Yesterday Melody's car, our 1995 Dodge Caravan, got new speakers fore and aft.
In the front we put Sony XS-R1311 speakers (5 1/4 inch, 3-way, 35 watts continuous).
These are apparently a "Wal-Mart model" quite similar to the
Yesterday Melody's car, our 1995 Dodge Caravan, got new speakers fore and aft.
In the front we put Sony XS-R1311 speakers (5 1/4 inch, 3-way, 35 watts continuous).
These are apparently a "Wal-Mart model" quite similar to the
 After much agony, we bought a pair of
After much agony, we bought a pair of
 So yesterday I had the rear speakers replaced with
So yesterday I had the rear speakers replaced with
 Here is how to control the background that users see while logging onto a
Windows computer, either locally or through Remote Desktop.
Here is how to control the background that users see while logging onto a
Windows computer, either locally or through Remote Desktop.